HTTPS Connectors
The Data Service can be accessible via HTTPS. The configuration of HTTPS is in .
|
Supported SSL Protocols
As of CloverDX Server 5.6 only TLS v1.2 protocol is supported by HTTPS connectors. |

As a key store, we support the Java Key Store (.jks) and PKCS #12 key store (.p12 or .pfx) formats.
As a trust store, we support the Java Key Store (.jks) format.
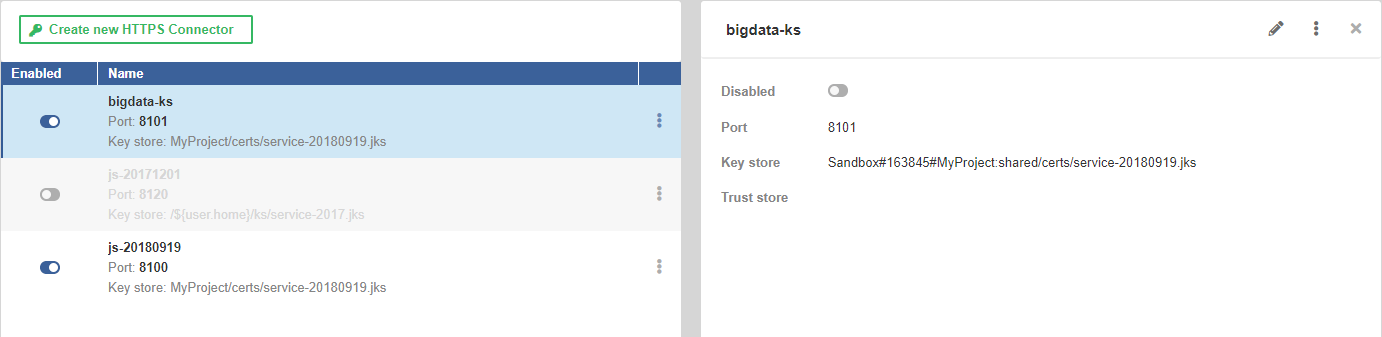
On the left hand side, there is a list of available HTTPS Connectors. On the right, there are details of the connector selected from the list. The New HTTPS Connector button creates a new HTTPS Connector.
List of HTTPS Connectors
The list of HTTPS Connectors shows available connectors. You can change the order by clicking on Name or Enabled in the header.
The button in the first column enables or disables the connector. Disabling the connector that is being used by Data Service makes the Data Service invalid.
The middle column shows the connector’s name, port, path to the key store and path to the trust store.
The … button offers an option to delete the connector.
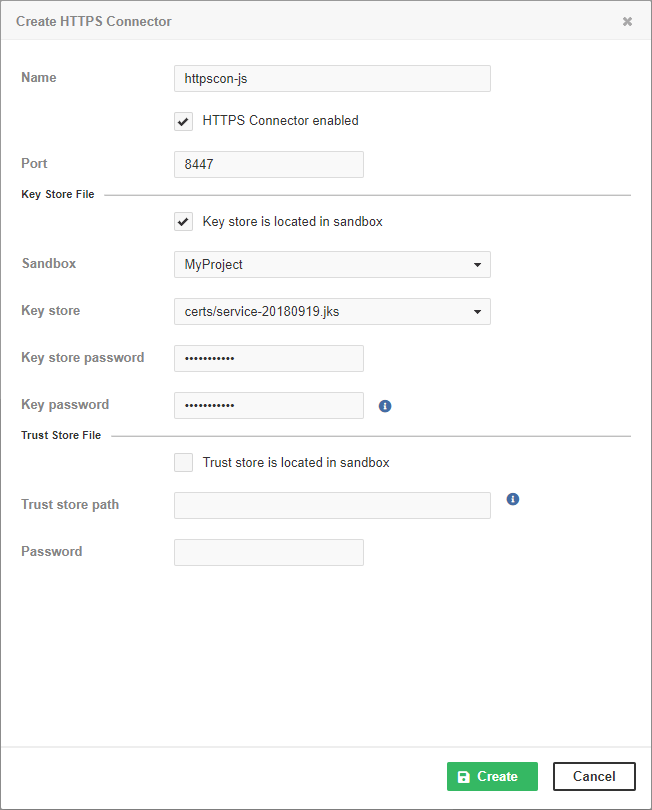
New HTTPS Connector
The New HTTPS Connector tab serves to create a new HTTPS Connector that can be used by one or more Data Services. One Data Service can use only one HTTPS Connector.
| Name | Description |
|---|---|
Name |
The name of the HTTPS Connector. The name should be unique. It is displayed in the list of HTTPS Connectors on the Endpoint’s Configuration tab. |
HTTPS Connector enabled |
The checkbox enables or disables the HTTPS Connector to listen on the specified port. Stopping an HTTPS Connector that is being used by a Data Service makes the Data Service invalid. |
Port |
The TCP port used by the HTTPS Connector. The port must not be occupied by another HTTPS Connector or any other program. If the Data Service is Deployed on CloverDX Cluster, it listens on this port on all Cluster nodes. If you use a firewall, set it to allow incoming connections to this port. If you use SELinux, it must be configured to allow CloverDX Server to use this TCP port. |
Key store is located in sandbox |
The checkbox switches between absolute paths to key store and paths relative to the Server sandbox. If selected, Sandbox and Key store items are displayed. Otherwise, you will see Key store path. The recommended way is to store the key stores out of the sandbox. |
Sandbox |
A sandbox with the key store. |
Key store |
The key store within the sandbox. |
Key store path |
An absolute path to the Java KeyStore.
You can use environment variables, system properties of JVM and configuration parameters of the Server as a part of the path.
Usually, you will use |
Key store password |
The password to the Java KeyStore. |
Key password |
The password to the key in the KeyStore. |
Trust store is located in sandbox |
The checkbox switches between absolute paths to trust store and paths relative to the Server sandbox. If selected, you can enter Sandbox and Trust store options. Otherwise, you will see Trust store path. |
Sandbox |
The sandbox containing the trust store. |
Trust store |
The trust store within the sandbox. |
Trust store path |
The absolute path to the trust store.
You can use environment variables, system properties of JVM and configuration parameters of the Server as a part of the path.
Usually, you will use |
Password |
The password to the trust store. |
To create a data service listening on HTTPS, you need a key store with a server certificate. You can create one with the following command:
keytool -keystore service.jks -genkey -keyalg rsa -keysize 3072 -alias serverNameAs a key store, we support the Java Key Store (JKS) (.jks) and PKCS #12 key store (.p12 or .pfx) formats.
As a trust store, we support the JKS (.jks) format.
For security reasons, we recommend you to put the key store outside the Server sandbox.
